FCSS_NST_SE-7.6 Exam Dumps - Fortinet NSE 6 - Network Security 7.6 Support Engineer
Searching for workable clues to ace the Fortinet FCSS_NST_SE-7.6 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s FCSS_NST_SE-7.6 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.
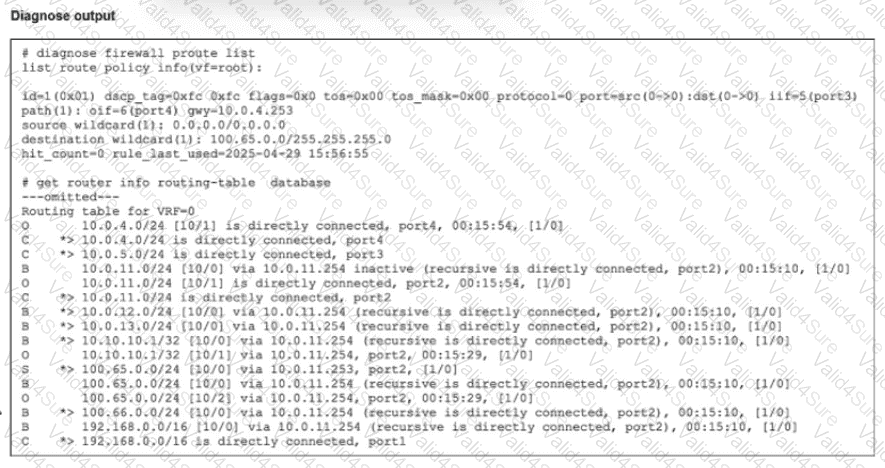
Which route will traffic take to get to the 100.65.0.0/24 network considering the routes are all configured with the same distance?
Refer to the exhibit.
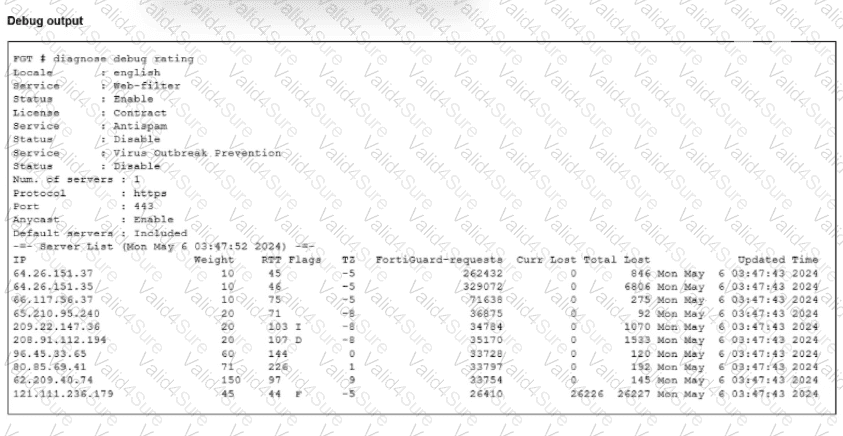
The administrator did not override the FortiGuard FODN or IP address in the FortiGate configuration
Which IP address did FortiGate get when resolving the servicem,fortiguard.net name?
Refer to the exhibit, which shows one way communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.
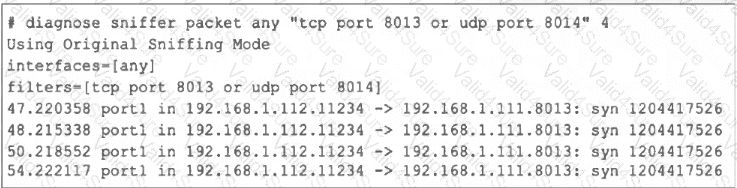
What three actions must you take to ensure successful communication? (Choose three.)
Exhibit 1.
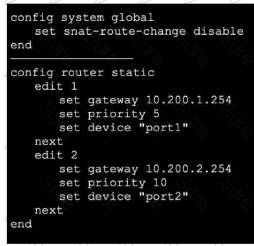
Exhibit 2.
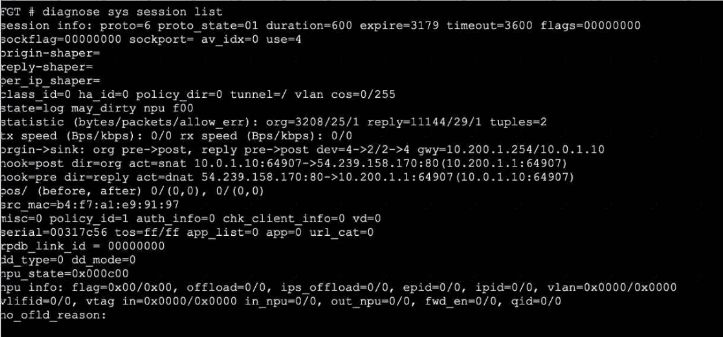
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
An administrator would like to lest session failover between the two service provider connections.
Which two changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
An administrator wants to capture encrypted phase 2 traffic between two FotiGate devices using the built-in sniffer.
If the administrator knows that there Is no NAT device located between both FortiGate devices, which command should the administrator run?
Refer to the exhibit.
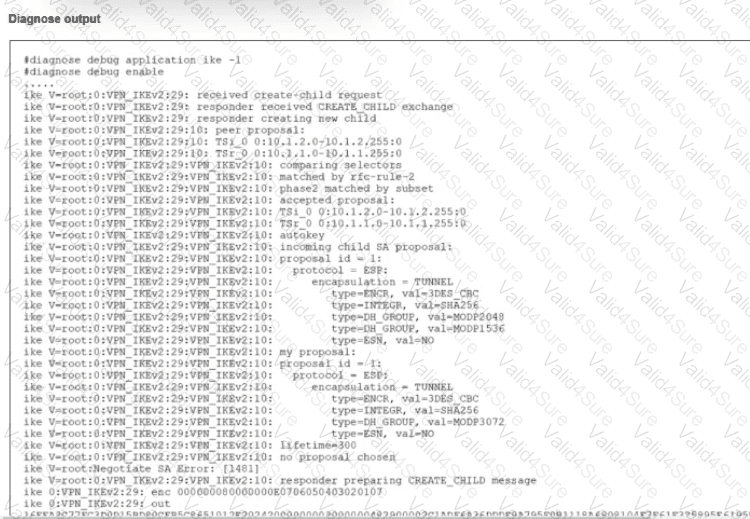
An IPsec VPN tunnel using IKEv2 was brought up successfully, but when the tunnel rekey takes place the tunnel goes down.
The debug command for IKE was enabled and, in the exhibit, you can review the partial output of the debug IKE while attempting to bring the tunnel up.
What is causing. The tunnel to be down?
Refer to the exhibit.
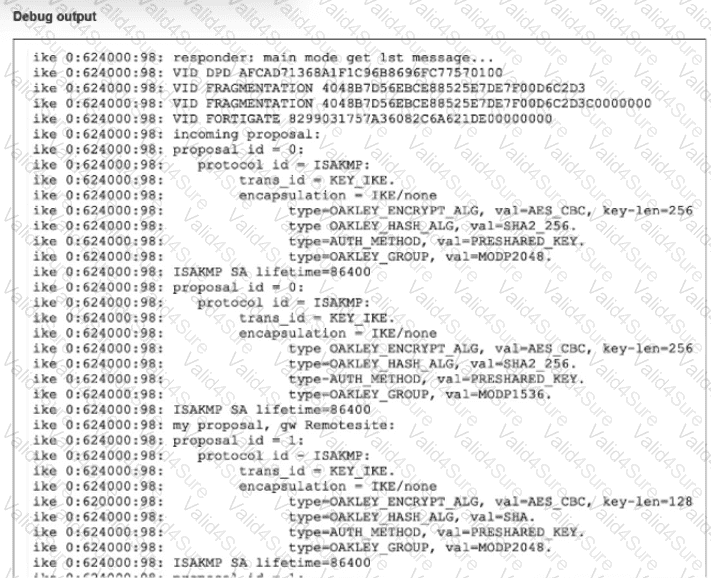
A partial output from an IKE real-time debug is shown
The administrator does not have access to (he remote gateway
Based on the debug output, which two conclusions can you draw? (Choose two.)