FCP_FGT_AD-7.6 Exam Dumps - FortiGate 7.6 Administrator FCP_FGT_AD-7.6
Searching for workable clues to ace the Fortinet FCP_FGT_AD-7.6 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s FCP_FGT_AD-7.6 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Refer to the exhibit.

Based on this partial configuration, what are the two possible outcomes when FortiGate enters conserve mode? (Choose two.)
What is the primary FortiGate election process when the HA override setting is enabled?
Which two statements are correct when FortiGate enters conserve mode? (Choose two.)
Refer to the exhibit.
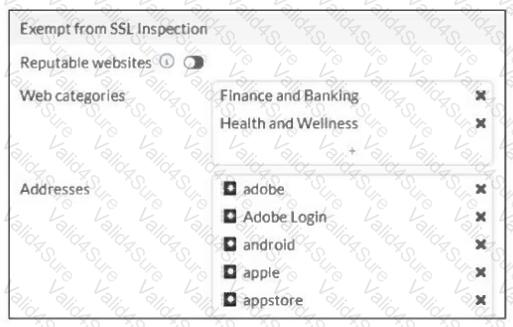
The predefined deep-inspection and custom-deep-inspection profiles exclude some web categories from SSL inspection, as shown in the exhibit.
For which two reasons are these web categories exempted? (Choose two.)
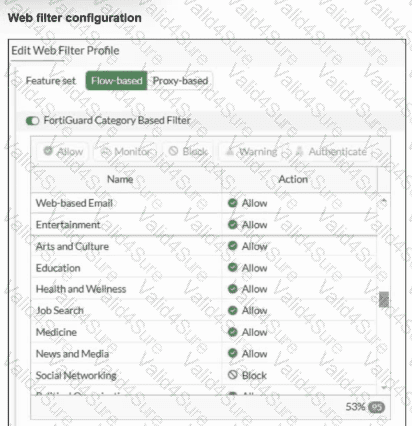
Refer to the exhibits.
An administrator configured the Web Filter Profile to block access to all social networking sites except Facebook. However, when users try to access Facebook.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibits, which configuration change must the administrator make to allow Facebook while blocking all other social networking sites?