EC0-350 Exam Dumps - Ethical Hacking and Countermeasures V8
Searching for workable clues to ace the ECCouncil EC0-350 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s EC0-350 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following network attacks relies on sending an abnormally large packet size that exceeds TCP/IP specifications?
Which of the following algorithms provides better protection against brute force attacks by using a 160-bit message digest?
Exhibit
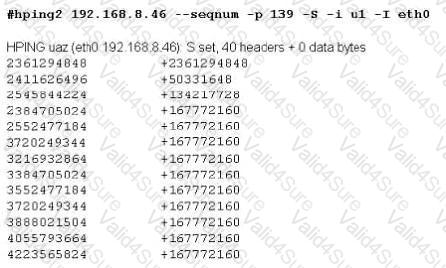
Joe Hacker runs the hping2 hacking tool to predict the target host’s sequence numbers in one of the hacking session.
What does the first and second column mean? Select two.
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
To what does “message repudiation†refer to what concept in the realm of email security?
Which of the following is considered an acceptable option when managing a risk?
Which of the following would be the best reason for sending a single SMTP message to an address that does not exist within the target company?