DS0-001 Exam Dumps - CompTIA DataSys+ Certification Exam
Searching for workable clues to ace the CompTIA DS0-001 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s DS0-001 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
(Which of the following is the purpose of including a COLLATE clause in a column definition?)
(A healthcare company relies on contact forms and surveys on its website to properly communicate with patients. To which of the following attacks is the company’s data most vulnerable?)
(A database administrator wants users to be able to access resources remotely from home. Which of the following best describes how the administrator can enable this access without compromising the security of the stored data?)
Which of the following is a characteristic of all non-relational databases?
Which of the following types of RAID, if configured with the same number and type of disks, would provide the best write performance?
A database administrator wants to remove inactive customers from a database. Which of the following statements should the administrator use?
A)
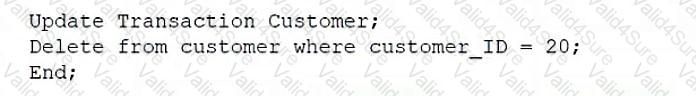
B)

C)

D)
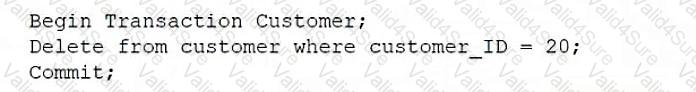
A company needs information about the performance of users in the sales department. Which of the following commands should a database administrator use for this task?