CTFL_Syll_4.0 Exam Dumps - ISTQB Certified Tester Foundation Level (CTFL) v4.0
Searching for workable clues to ace the iSQI CTFL_Syll_4.0 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CTFL_Syll_4.0 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Which of the following statements about white-box test techniques is true?
The following chart represents metrics related to testing of a project that was competed. Indicate what is represented by tie lines A, B and the axes X.Y
A)
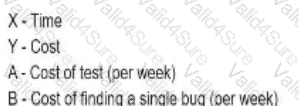
B)

C)
D)

Which ONE of the following roles is responsible for mediating, managing time, and generating a safe review environment in which everyone can speak freely?
Use Scenario 1 “Happy Tomatoes†(from the previous question).
When running test caseTC_59, the actual result fort = 35degrees Celsius isOUTPUT = Xinstead of the expected output.
Which information should NOT be included in the defect report?
In addition to thorough testing of the requirements specification, a development team aims to involve users as early as possible in the development process, using practices such as prototyping, to ensure that the software systems being developed will meet the users’ expectations. This approach is especially useful at mitigating the risks associated with one of the seven testing principles, which one?
Consider the following examples of risks identified in different software development projects:
[I]. The contrast color ratio for both normal text and large text of a website does not comply with the applicable accessibility guidelines, making it difficult for many users to read the content on the pages
[II]. A development vendor fails to deliver their software system on time, causing significant delays to system integration testing activities that have been planned as part of a development project for a system of systems
[III]. People in the test team do not have sufficient skills to automate tests at the test levels required by the test automation strategy which does not allow production of an effective regression test suite
[IV]. In a web application, data from untrusted sources is not subject to proper input validation, making the application vulnerable to several security attacks
Which of the following statements is true?