CFR-210 Exam Dumps - Logical Operations CyberSec First Responder
Searching for workable clues to ace the Logical Operations CFR-210 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s CFR-210 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
A SOC analyst reviews vendor security bulletins and security blog articles against the company’s deployed system and software base. Based on current attack patterns, three vulnerabilities, including a zero-day vulnerability, have been upgraded to high priority. Which of the following should the SOC analyst recommend? (Choose two.)
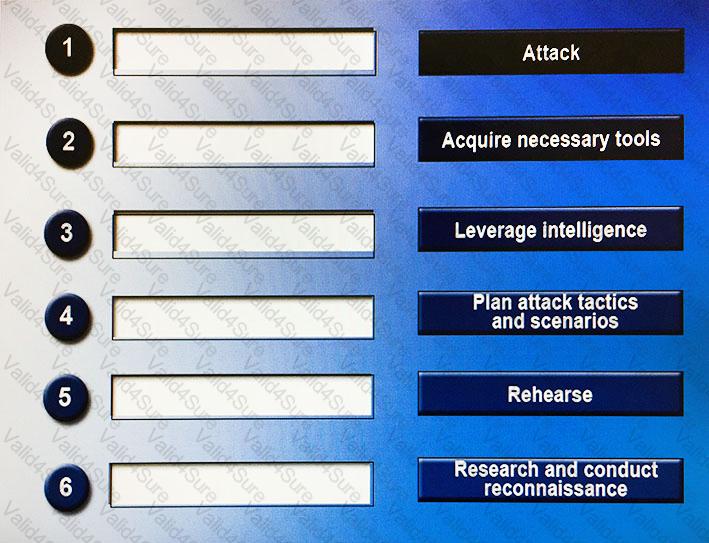
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
An incident responder is asked to create a disk image of a compromised Linux server. Which of the following commands should be used to do this?
An attacker has decided to attempt a brute force attack on a UNIX server. In order to accomplish this, which of the following steps must be performed?
An attack was performed on a company’s web server, disabling the company’s website. The incident response team’s investigation produced the following:
1. Presence of malicious code installed on employees’ workstations.
2. Excessive UDP datagrams sent to a single address.
3. Web server received excessive UDP datagrams from multiple internal hosts.
4. Network experienced high traffic after 3:00 pm.
5. Employee workstations sent large traffic bursts when employees accessed the internal timecard application.
Which of the following BEST describes the attack tool used to perform the attack?