C1000-116 Exam Dumps - IBM Business Automation Workflow V20.0.0.2 using Workflow Center Development
Searching for workable clues to ace the IBM C1000-116 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s C1000-116 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
In the Process Inspector, what happens when the administrator puts an activity to a SKIPPED state?
Available Choices (select all choices that are correct)
When a JavaScript error has occurred on a page developed in Business Automation Workflow, where should a developer view this error?
Available Choices (select all choices that are correct)
Which identity governance and access management method is pre-integrated with the starter deployment of Cloud Pak for Business Automation?
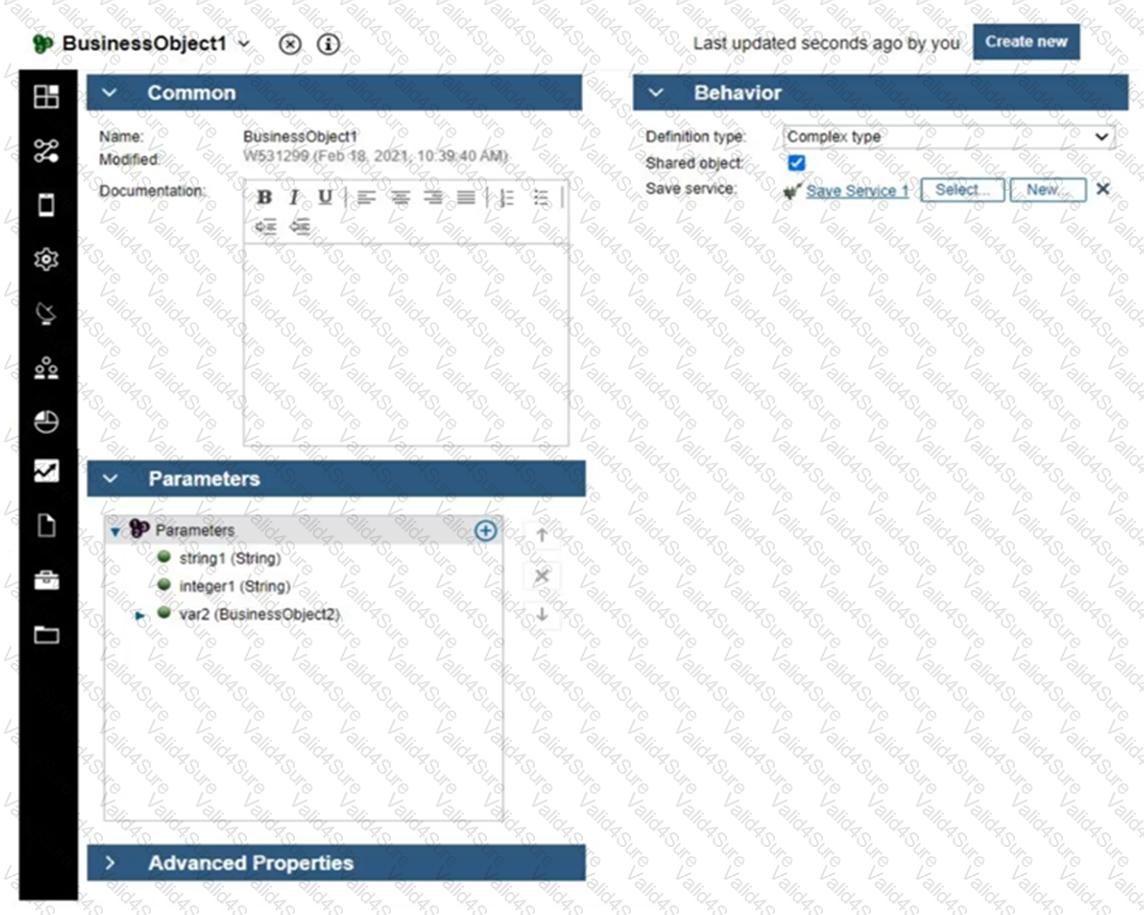
What are two uses of the Save service implementation under the Behavior tab in the business object definition shown below? (Choose two.)
Which feature in OpenShift Container Platform allows developers to seamlessly provision resources provided by a variety of service brokers?