AZ-104 Exam Dumps - Microsoft Azure Administrator
Searching for workable clues to ace the Microsoft AZ-104 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s AZ-104 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
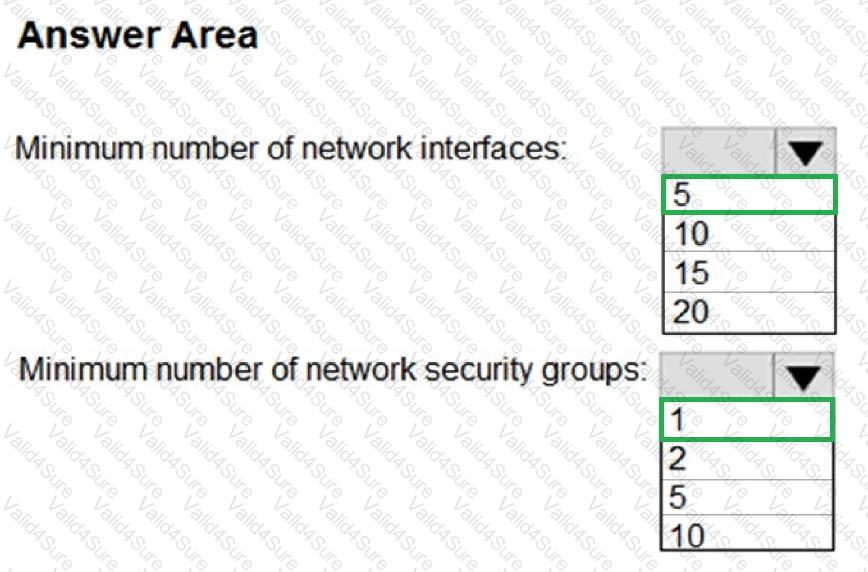
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network interfaces and network security groups that you require? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have an Azure subscription.
Users access the resources in the subscription from either home or from customer sites. From home, users must establish a point-to-site VPN to access the Azure resources. The users on the customer sites access the Azure resources by using site-to-site VPNs.
You have a line-of-business app named App1 that runs on several Azure virtual machine. The virtual machines run Windows Server 2016.
You need to ensure that the connections to App1 are spread across all the virtual machines.
What are two possible Azure services that you can use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
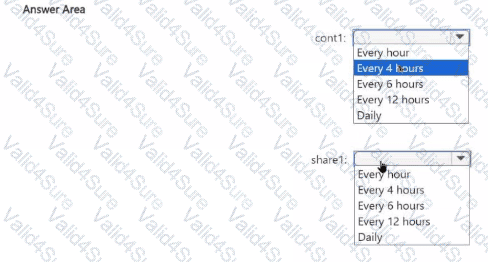
You need to configure Azure Backup to meet the technical requirements for cont1 and share1.
To what should you set the backup frequency for each resource? To answer, select the appropriate options in the answer area. Â
NOTE: Each correct selection is worth one point. Â
You implement the planned changes for cont2.
What is the maximum number of additional access policies you can create for cont2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

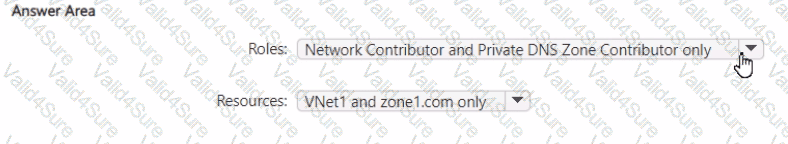
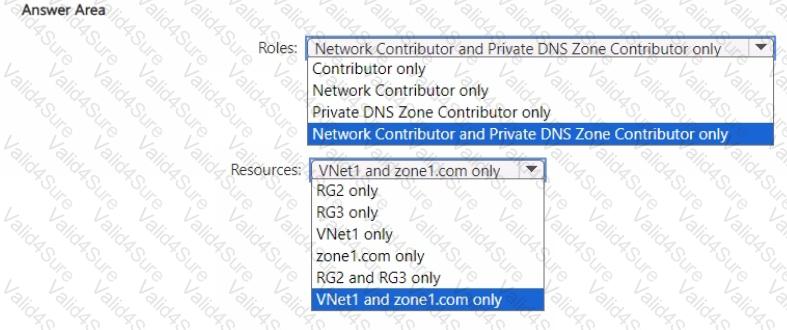
You need to implement the planned changes for User1.
Which roles should you assign to User1, and for which resources? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have an Azure App Service app named App1 that contains two running instances.
You have an autoscale rule configured as shown in the following exhibit.
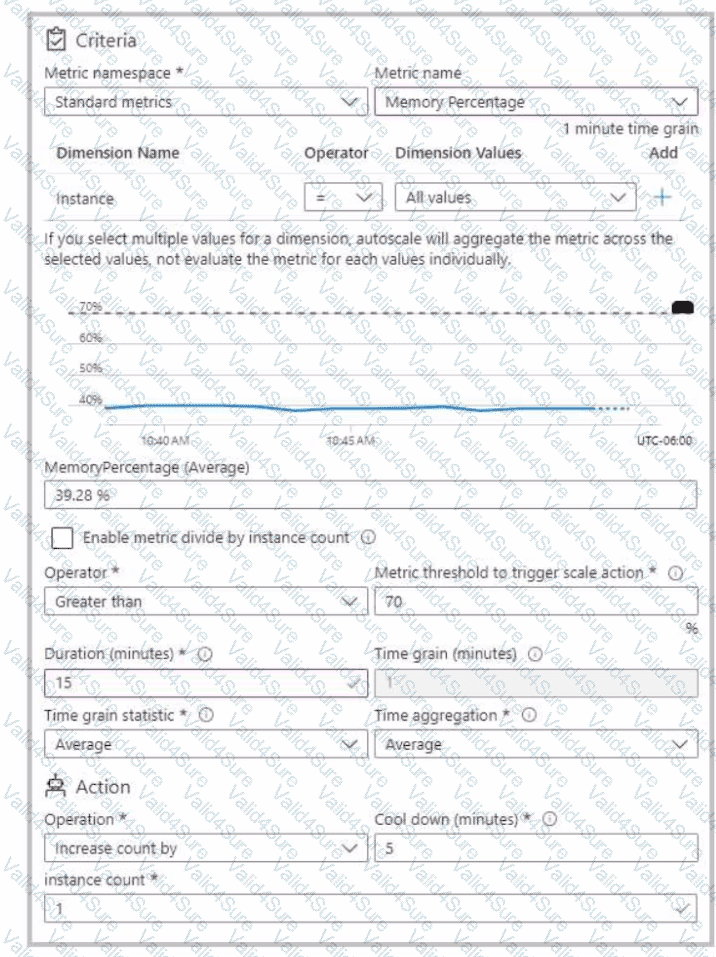
For the Instance limits scale condition setting, you set Maximum to 5.
During a 30-minute period, App1 uses 80 percent of the available memory.
What is the maximum number of instances for App1 during the 30-minute period?
You need to define a custom domain name for Azure AD to support the planned infrastructure.
Which domain name should you use?
You discover that VM3 does NOT meet the technical requirements.
You need to verify whether the issue relates to the NSGs.
What should you use?