352-011 Exam Dumps - Cisco Certified Design Expert Practical Exam
Searching for workable clues to ace the Cisco 352-011 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 352-011 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
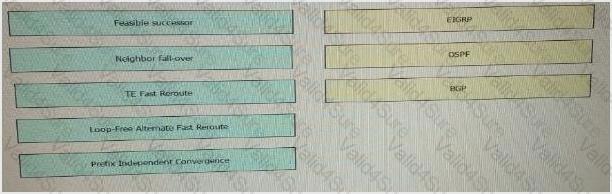
Drag the fast Reroute mechanism on the left and drop it onto the corresponding routing protocol on the right
You are redesigning a single-level IS-IS network with 500 routers, which have short-haul and long-haul links Most of the time the routing domain is stable, but periodically interfaces on long-haul links bounce for a short period of time , causing 10 to 20 flaps in a few minutes. The probable cause is local road construction. Although fast convergence important, the client has concerns about taxing CPU cycles on the older routing platforms. What change should you recommend that both protects the CPU of the older routers during the short periods of excessive flapping, yet does not have an impact on fast convergence for all interface failures?