300-620 Exam Dumps - Implementing Cisco Application Centric Infrastructure (300-620 DCACI)
Searching for workable clues to ace the Cisco 300-620 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 300-620 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
When creating a subnet within a bridge domain, which configuration option is used to specify the network visibility of the subnet?
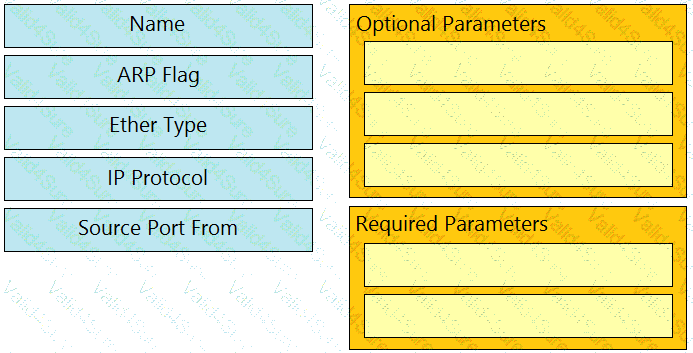
Drag and drop the Cisco ACI filter entry options from the left onto the correct categories on the right indicating what are required or optional parameters.
Which two protocols support accessing backup files on a remote location from the APIC? (Choose two.)
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
An engineer deploys a two-pod Cisco ACI Multi-Pod environment. Why should no more than two Cisco APIC controllers be deployed in the same pod?