100-160 Exam Dumps - Cisco Certified Support Technician (CCST) Cybersecurity
Searching for workable clues to ace the Cisco 100-160 Exam? You’re on the right place! ExamCert has realistic, trusted and authentic exam prep tools to help you achieve your desired credential. ExamCert’s 100-160 PDF Study Guide, Testing Engine and Exam Dumps follow a reliable exam preparation strategy, providing you the most relevant and updated study material that is crafted in an easy to learn format of questions and answers. ExamCert’s study tools aim at simplifying all complex and confusing concepts of the exam and introduce you to the real exam scenario and practice it with the help of its testing engine and real exam dumps
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
Which security measure can prevent unauthorized devices from automatically connecting to a corporate network through unused switch ports?
Your supervisor tells you that you will participate in a CVSS assessment.
What will you be doing?
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
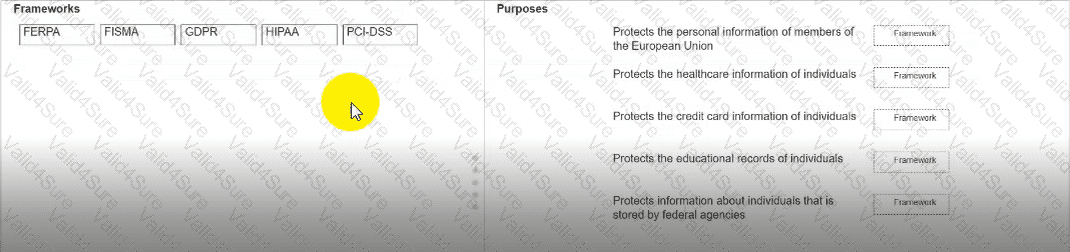
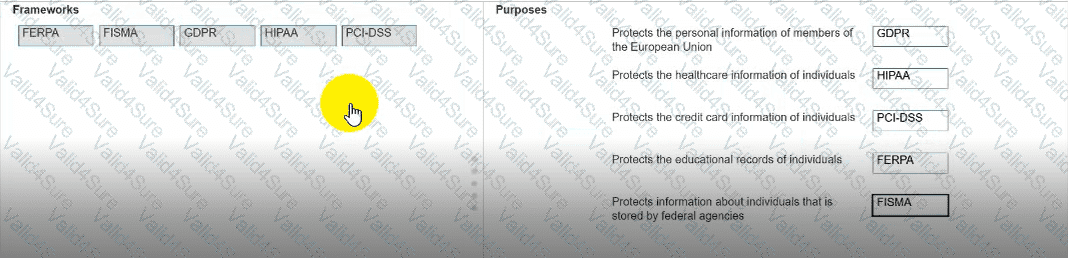
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.